Sections of the site
Editor's Choice:
- What is an MTS trust payment?
- Aeroflot Bonus program: how to accumulate miles and what can you spend them on?
- How to find out which drive is on your computer: SSD or HDD How to find out which ssd is on your computer
- Testing Fractal Design Define R5 Fractal Design Define R5 - Quiet, spacious
- How to speed up Android smartphone and tablet?
- Flood Control VKontakte: we tell you why the problem occurs and how it can be removed. So flood control
- Charger based on an ATX power supply Laboratory power supply based on a 3528 PWM controller
- What to do if the wire does not charge your iPhone
- Virtual machine for Mac Virtual windows on mac os
- About Tele2 service How to enter payment confirmation to number 312
Advertising
| How to block access to Internet applications. How to Manage Permissions for Individual Apps on Android |
|
The inviolability of confidential data and the safety of the privacy of Android device owners directly depend on the installed applications, or, more precisely, on the permissions that are granted to them. Many users who assign certain permissions to new applications on Android may become confused, not having sufficient knowledge of certain concepts and processes. Why does an application that does not perform the corresponding tasks request access to the camera, phone book, and even quick messages? The answer is clearly ambiguous. We suggest mentioning the scandal that arose last year related to permits for Facebook Messenger. If you pay attention to all the permissions it asks for this program, you can come to the conclusion that she can manage her personal life without your knowledge. As it turned out later, the root of the problem lay in the intricacies of the architecture of Android programs, since applications with different purposes request extremely similar permissions. To operate, for example, a flashlight, you need to obtain permission to take photos and videos without appropriate confirmation from the user. The bottom line is that the LED diode, which is used as a flashlight, is an integral part of the smartphone camera circuit. If the program has access to the flashlight, it means that photo and video recording is also open to it, which is why the request for these permissions appears. However, self-interested application creators also include in the list of permissions those that allow you to count on profit thanks to donations (internal purchases). Such cases can be quite risky if you do not have a password for making purchases in the Market. Obtain permissions for functions such as program history, phone book, location identification, specific to clients social networks, browsers, navigators. But under no circumstances should they be present in games, or, as stated earlier, in “flashlights”. Exercise extreme caution in relation to free applications, since they can transfer personal data to third parties or are “stuffed” with advertising from top to bottom. It is recommended to carefully research the required permissions when installing programs to avoid becoming a victim of deception. Also remember the fact that spending a dollar on an app is a wiser move than giving dozens of permissions to other free alternatives. Don't install applications that are not particularly important to you. Taking the time to carefully review all required permits will help ensure that risks are minimized as much as possible. Permission Master is a special module for the Xposed Framework, which is designed to manage the permissions of any program installed on your gadget. Detailed description this project with step by step instructions I did a tutorial on installing Xposed and individual modules for it in , so we won’t repeat ourselves again, but let’s move on directly to the work of Permission Master.
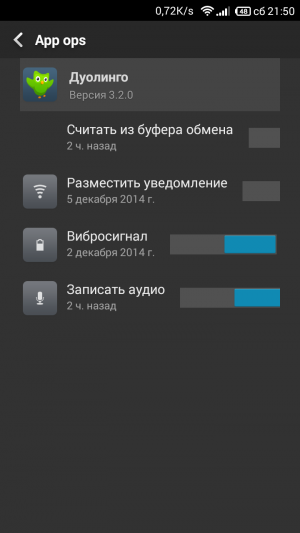
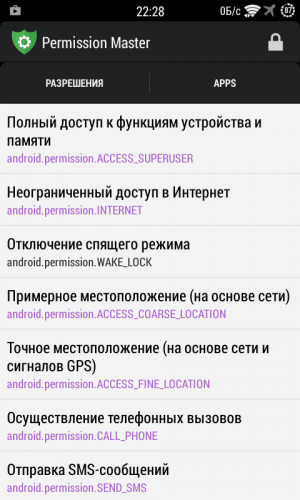
After installing the module and restarting the device, you will find a new icon in the application list in the form of a green shield with a gear. We launch the program and see a window divided into two tabs. The first contains the names of all available permits. Tapping on any name in the list shows us all programs that have this property. Another tap, and the program name becomes red and crossed out - this means that the corresponding permission has been disabled.
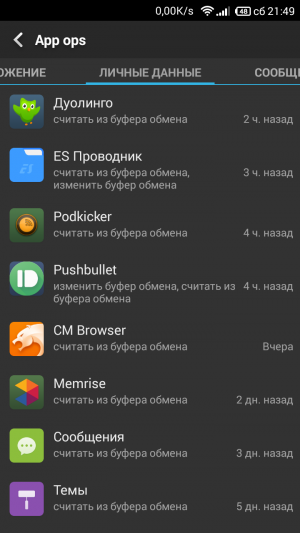
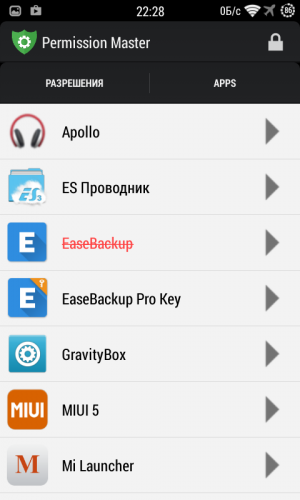
Approximately the same algorithm is used on the second tab, but here all permissions are grouped by program. You can view the list of available actions for each application and disable unnecessary ones with one tap. Please note that if you hold your finger over the name of any resolution, a pop-up window will appear explaining its properties. This will be very useful for those who doubt the necessity and safety of a particular action. And to protect yourself from additional problems, do not forget to go to the Permission Master settings and disable the display of system programs. The Permission Master app will be useful for all advanced Android users who want to have full control over installed applications. Now you will have the opportunity to disable tracking functions, close those programs that do not need it at all, ban your smartphone and much, much more that is not available to ordinary Android users. At the time of installation, each program requests from us the rights to perform the actions necessary for its functioning. As a rule, we agree to this request without going into too much detail, but simply relying on the good faith of the application developers. In this article, you will learn how to correct the situation and take control of permissions for programs installed on your smartphone. First of all, you need to explain why you might want to limit the capabilities of certain programs. First of all, this is necessary for safety reasons. If an innocent calculator or flashlight requests unrestricted network access and tries to read your address book, then this is at least suspicious. And secondly, you can change the functionality of some programs this way. For example, by blocking network access for applications that do not require it to perform their basic tasks, you can get rid of intrusive advertising. Google in Android version 4.3 included operating system special system utility App Ops for permission management installed programs. However, it is intended for developers and is hidden from view ordinary users. In subsequent releases of Android, this utility was hidden even deeper in the depths of the system, so it was created by independent developers special utility, making it easier to access App Ops.
After installing and activating this module in the Xposed Framework, you will need to reboot your device. The Permission Master interface consists of two tabs, the first of which lists all available permissions, and the second of which is the programs you have installed. This way you can quickly check what rights each program has and, if necessary, quickly disable unnecessary ones. The standard procedure for installing programs in the Android operating system requires that you either agree to the application's request or cancel its installation. Using the methods described in this article, you can do the smart thing - first install the program you need, and then leave only those rights that it actually needs. Android has a very good security mechanism called the app permission system. Essentially, it is a set of actions that the system allows an application to perform. The fact is that by default, all applications in Android run in an isolated environment - the so-called “sandbox”. And in order to do anything with something, so to speak, public, they need to get permission. These permissions are divided into several categories, but we are only interested in two of them - “Normal” and “Dangerous”. The “Regular” group includes things like accessing the Internet, creating shortcuts, connecting via Bluetooth, and so on. These permissions are granted to applications without requiring user consent, meaning the system doesn't ask you anything. But in order to obtain one of the “dangerous” permissions, the application must ask the device owner if he agrees to issue it. What are the dangers of “dangerous” permissions and is it worth issuing them to applications? Let's figure it out. Dangerous PermissionsThe “Dangerous” category includes nine groups of permissions that are in one way or another related to the security of user data. In turn, each of the groups contains several permissions that an application can request. If the user has already approved one of the permissions in this group, the application will receive all other permissions from the same group automatically - without a new request to the user. For example, if an application has already requested and received permission to read SMS, then it will subsequently automatically will receive permission to send SMS, receive MMS, and all other permissions from this group. Calendar
What is dangerous: If you actively use an electronic diary, then access to it will allow you to find out everything about what you did in the past, are doing today and are going to do in the future - a real find for a spy. Also, some crookedly written application can inadvertently erase important meetings from the calendar. CameraWhat is dangerous: Allows the application to follow all your movements. For example, scammers may find out that you went on vacation and try to visit your home. Microphone
What is dangerous: The application will be able to audio record everything that happens near the smartphone. All your conversations. Not just by phone. Telephone
What is dangerous: By giving an application permission from this group, you allow it to perform almost any action related to voice communication. The application will be able to find out when and who you called. Or call anywhere at your expense, including to “very paid” numbers. Sensors
What is dangerous: Allows an application to monitor what's happening to your body using information from sensors in the appropriate category, if you have and use them (smartphone motion sensors are not included in this category). SMS
What is dangerous: Allows an application to receive and read all your text messages. And also send SMS (of course, at your expense) - for example, to sign you up for some paid “service”. Memory
What is dangerous: Gives the application the ability to read, change and delete any of your files stored in the smartphone's memory. How to set app permissionsYou should be careful about the permissions an application requests. If a game or photo app is requesting access to your current location, this is most likely not normal - such apps this information to nothing. But the navigation application really needs GPS - but, in turn, there is absolutely no need to give it access to contacts or SMS, for example. If the rights that an application requests look too suspicious, it is better not to install such an application at all If the rights that an application requests look too suspicious, it is better not to install such an application at all. Or you can simply not allow him access to those functions and data that you do not want to share. In Android version 6 and newer apps display a request to the user at the moment when they need one or another of the “dangerous” permissions. If you don't agree to allow the application access, then you can simply click the "Decline" button. However, if the application really needs one or another permission, errors may occur in its operation.
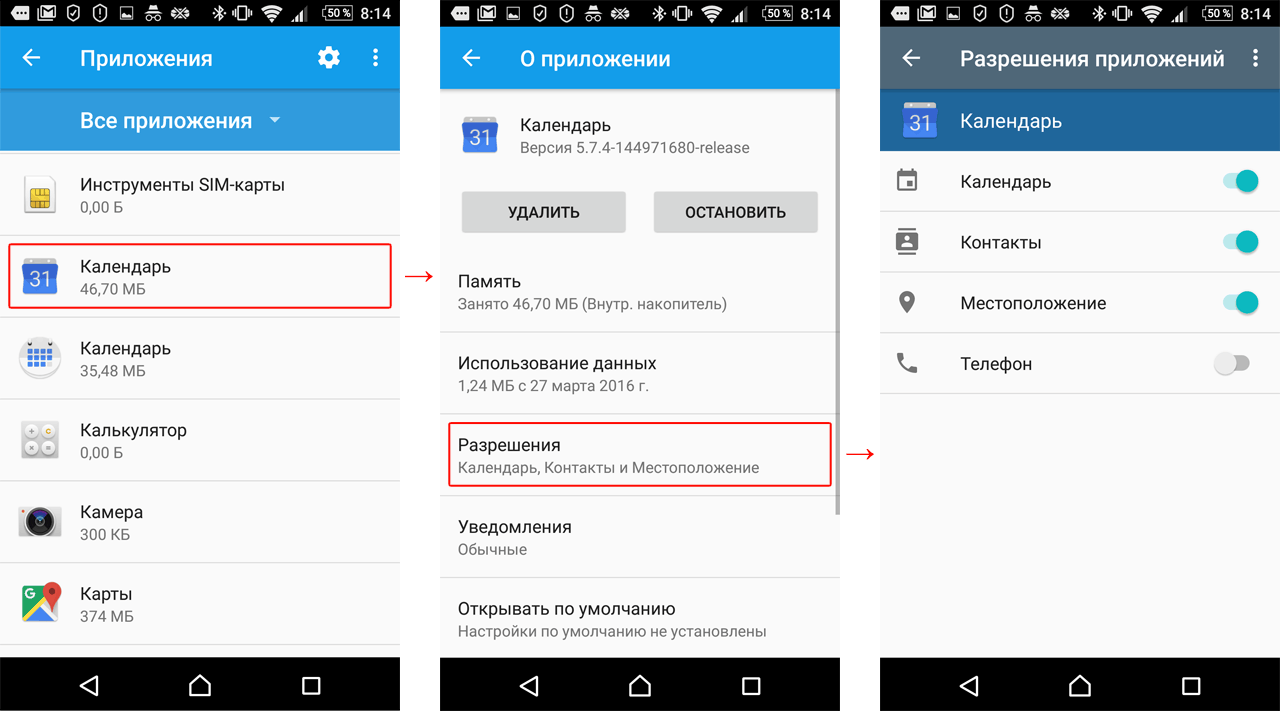
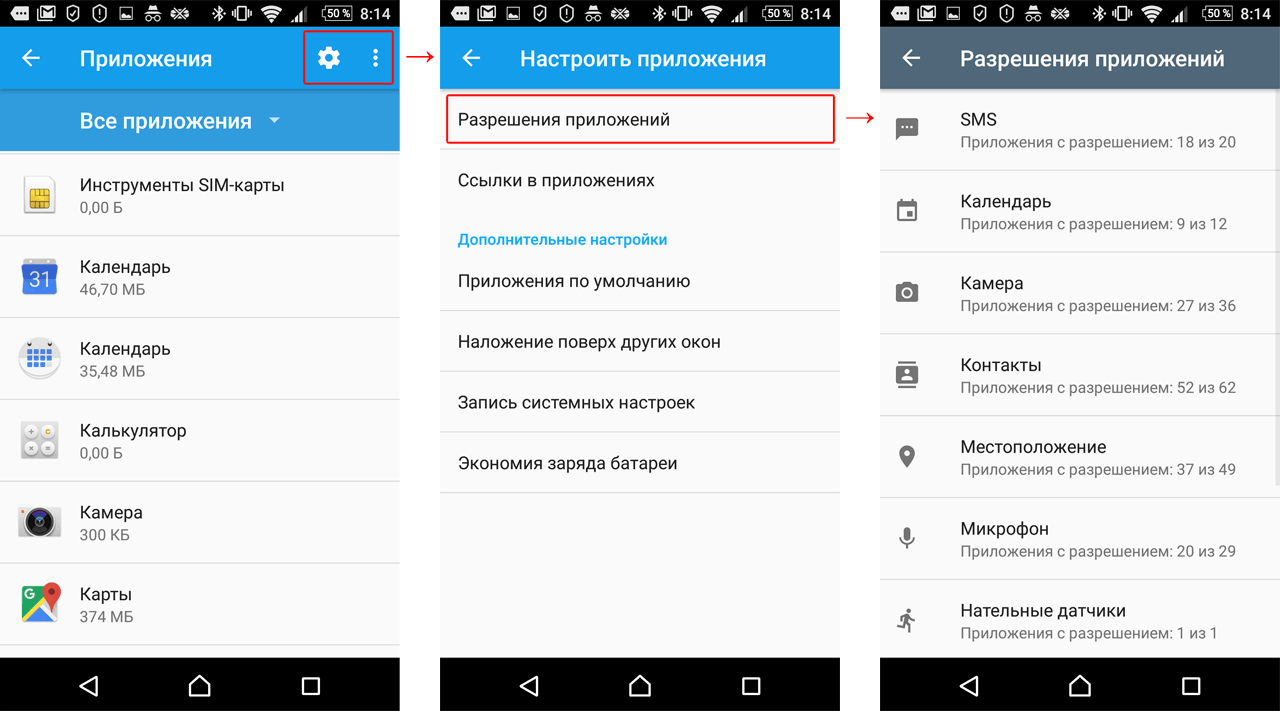
In addition, the list of granted permissions can be checked and changed at any time in the operating system settings. To do this, go to Settings -> Applications.
Secondly, you can look at full list applications that have requested or may request one of the “dangerous” permissions. For example, find out which applications would be willing to ask you for access to contacts and which ones are already allowed, and also deny this to those that you don’t trust. To do this, click on the gear in the upper right corner and select Application Permissions.
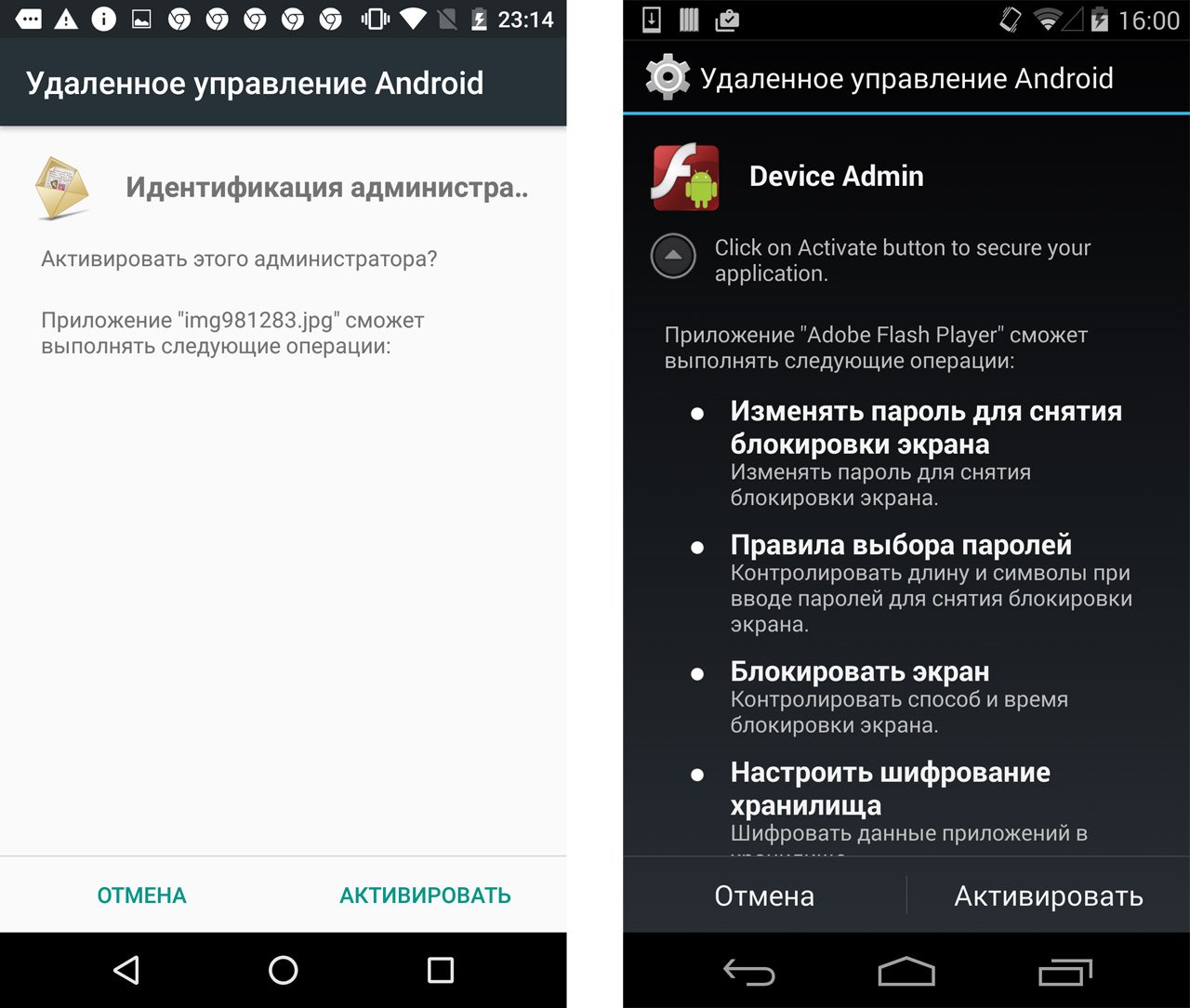
Thus, an application, for example, to send an SMS, will need to ask the user for permission once, after which the user can deny this right to the application at any time, simply by moving the circle in the settings. Special rightsIn addition to the permissions that fall under the "Dangerous" category, there are a few other app permissions in Android that are worth knowing about. If any application requests such rights, this is a reason to think carefully and check whether you have encountered a Trojan. AccessibilityHaving these permissions in an app allows it to make the app or device easier to use for users with disabilities such as low vision or hearing problems. But at the same time Android system is designed in such a way that the same set of capabilities turns out to be a very convenient tool for malicious applications. With these rights, Trojans can intercept data from other applications, including user-entered text. In addition, using these capabilities, malware can even buy applications from Google Play Store. Default SMS applicationMany Trojans try to become the default SMS application, because this allows them not only to read SMS, but also to hide them from the user, even in modern Android versions. For example, Trojans may need this to intercept one-time codes to confirm banking transactions. Rights to display your window on top of other applicationsWith these rights, Trojans can display their phishing windows on top of other applications, such as mobile banking or social networks. It seems to you that you are entering your username and password into the window of a real application - but in fact this is happening in a fake window created by the Trojan, and the data account leak to the attackers. Device administrator rightsWith these rights, the application can, among other things, change the password, lock the camera, or even delete all data from the device. Many Trojans request these rights because the application that is the device administrator is much more difficult to remove.
Superuser rightsThese are the most dangerous rights. In normal mode, Android does not allow an application to obtain such rights, but some Trojans are able to obtain superuser rights themselves by exploiting vulnerabilities in the system. The most unpleasant thing is that if an application has superuser rights, it depreciates all other protective mechanisms: by taking advantage of these rights, the malware can perform any action in the system, regardless of what permissions it has been given. It is worth noting that even new system The permissions feature introduced in Android 6 does not protect against malware, it only provides the user with the ability to prevent loss of data or money. For example, the Gugi Trojan persistently requests the user's rights to override other applications, justifying this by the need to work with windows. Having received these rights, the Trojan blocks the operation of the device with its window until it receives all the other rights it needs. ConclusionNot all apps should be allowed to do whatever they want on your smartphone. And it is better not to give some permissions at all - fortunately Android 6 and later allows this. However, there are some applications that really need a lot of different rights. For example, antivirus programs In order to work properly, be able to scan the system and proactively protect against threats, you need not only permission to access files, but also much more. However, you should not blindly grant permissions even to applications that you trust. Just before you give these permissions, consider whether this particular application really needs them. Such vigilance, however, does not protect against the fact that some malware will gain rights itself through vulnerabilities in the system. Therefore, it is important not only to correctly configure permissions for relatively “peaceful” applications hunting for your personal data, but also to have a means to detect much more dangerous “violent” malware - do not forget to install a reliable antivirus on your Android device. Every time we install a new application on Android, it asks for our consent to allow certain actions. Most often, no one pays attention to this list of permissions. We agree and continue the installation, hoping that the application has been verified and cannot cause any harm. In this article we will tell you what application permissions are on Android and how to manage them. What are application permissions on AndroidAndroid applications can have access to system hardware and software resources. For example, access to location tracking, camera and audio recording, making calls, payments, and so on. During installation of an application, we can see a list of permissions that it requires. No application will be installed without our consent to grant these permissions. You can also view application permissions on Android immediately before installing them:
You should be wary of applications that ask for permission to perform actions that are uncharacteristic of them. For example, when an application to turn on a flashlight requests access to the Internet and tries to read your messages. It is worth noting that in many cases, Internet access is needed solely for loading advertisements into the application, so in the case of a flashlight application, Internet access can be prohibited. Manage application permissionsManaging application permissions became possible for the first time with the release of Android 4.3; for this purpose, the App Ops utility was added to the system. But access to it was denied through the settings, since it was intended exclusively for developers. Starting from Android 5.0, gain access to manage permissions for regular user It has become even more difficult, but already in Android 6, developers have given everyone the opportunity to manage application permissions through the device settings. Application permissions on Android 4.3-4.4If you have a smartphone with Android version 4.3-4.4, then the AppOps utility will help you gain access to managing application permissions. The procedure is as follows:
Application permissions on Android 5.0-5.1if you have Root is right a (you will be able to manage the permissions of all applications, system and third-party):
If you do not have Root rights (you will only be able to manage permissions of third-party applications):
After that, in App Ops - Permission manager, you can configure permission settings for a specific application at your discretion. How do you control application permissions on Android? Write your options for the comment. Answers on questionsAfter setting permissions, the application crashed, what should I do?This can happen if the application is written under more old version Android than on your device. If the application crashes, go to permission management and re-enable the permission that you disabled. After this, the application will work normally. |
Popular:
New
- Aeroflot Bonus program: how to accumulate miles and what can you spend them on?
- How to find out which drive is on your computer: SSD or HDD How to find out which ssd is on your computer
- Testing Fractal Design Define R5 Fractal Design Define R5 - Quiet, spacious
- How to speed up Android smartphone and tablet?
- Flood Control VKontakte: we tell you why the problem occurs and how it can be removed. So flood control
- Charger based on an ATX power supply Laboratory power supply based on a 3528 PWM controller
- What to do if the wire does not charge your iPhone
- Virtual machine for Mac Virtual windows on mac os
- About Tele2 service How to enter payment confirmation to number 312
- Working with internal memory EEPROM Eeprom erasing