Sections of the site
Editor's Choice:
- Decided to switch from Windows to Mac?
- How to use Google Photos, overview of Google foto login functions
- Payment system Payza (ex-Alertpay) Payza login to your personal account
- How to open APK and how to edit?
- Review of the Alpha GT smartphone from Highscreen Packaging and delivery
- Official LG firmware via KDZ
- What is an SSD and how to install it?
- How to put an accent on a letter in Word
- How to convert images to PNG format?
- Technical problems and their solutions v
Advertising
| Software for working with the network. What do routing rules that form a loop look like? This can be solved by sending special packages |
|
The Windows operating system has many auxiliary tools for diagnostics and configuration local network and Internet access. Most of them are intended mainly for system administrators. But some may also be useful to ordinary home users. These tools are programs (commands) command line. To use them, you must first open a command prompt window ( Start — Programs(All programs) - Standard — Command line). Windows Internet Protocol Configuration Tool (ipconfig)To view network connections you can use the command ipconfig. To do this, on the command line, enter ipconfig and press Enter. The utility will display information in the window about all network connections, which contain , subnet mask and gateway IP address. Local network connections that are not used to access the Internet may not have a gateway address. If the computer has direct connection to the Internet, then the displayed address corresponds to the address of the computer on the Internet. If the computer is connected through a router, the displayed address may differ from the address used to access the Internet. PingTeam ping designed to be sent to a designated address to measure response time. With its help, you can determine whether the destination address is accessible, the quality of communication in terms of loss of transmitted information and delivery speed. To use the command, enter at the command line ping<hostname> <hostname> ping yandex.ru). The result of the command will contain information about the address of the computer being pinged, the amount of information transmitted and the response time, as well as statistical (total) information on all sent packets. Tracing (tracert)Team tracert is intended to determine the route along which information is delivered to the specified address. With its help, you can determine through which network segments information is transmitted, and, if there is no connection with the specified computer, determine the location of the “break.” To trace the route, enter at the command line tracert<hostname> and press the Enter key, where instead <hostname> you should specify the domain name or IP address of the computer (for example, tracert yandex.ru). As a result, a list of nodes will appear in the command line in the form of response time (ping) and IP addresses through which Internet packets pass when delivered to their destination. Path pingTeam pathping is a collection of traces and pings to each route node. It allows you to determine on which node the loss of packets occurs during their transmission to their destination. To use the command, enter at the command line pathping <hostname> and press the Enter key, where instead <hostname> you should specify the domain name or IP address of the computer (for example, pathping yandex.ru). When executing the command, it will first trace and then ping each node in the trace. A command execution report will be displayed in the command line window. Executing this command can take up to 5-10 minutes due to the large number of pings. Network connection statistics (netstat)Team netstat displays information about active Internet connections on the computer. For more information, enter on the command line netstat-a and press Enter. After executing the command, the command line will display information about active connections in the form of the protocol used, local IP address and port, remote IP address and port, and connection status. If your computer has open ports, then the command will display information about them as well. Diagnostic utilities. To test the functionality of the TCP/IP stack, Windows XP includes a number of command line utilities, each of which is responsible for testing the functionality of a specific part of the TCP/IP stack. ipconfig utility. The ipconfig utility is designed to display TCP/IP configuration parameters and control the receipt of parameters from the DHCP server. It has the following syntax: ipconfig | /release | /flushdns | /displaydns | /registerdns | /showclassid adapter | /setclassid adapter ] A description of the ipconfig utility keys is given in the table:
When you call the ipconfig utility without parameters, brief information about all connections configured to use the TCP/IP protocol is displayed. Displayed: IP address, subnet mask and default gateway. As a parameter adapter the name of the connection is indicated. You can use masks when specifying connection names. When you specify a mask, information is displayed regarding all connections that match the mask. ping utility. The ping utility is designed to send an echo request to a remote host and receive a response from it. It has the following syntax: ping [-t] [-a] [-n quantity] [-l size] [-f] [-i TTL] [-v TOS] [-r quantity] [-s quantity] [ [-j host_list] | [-k host_list]] [-w timeout] host_name A description of the ping utility keys is given in the table.
Utility ping displays information for each request sent to the specified host. Below is a typical example of a ping response. Exchange of packets from 172.16.6.20 to 32 bytes: Reply from 172.16.6.20: number of bytes=32 time Reply from 172.16.6.20: number of bytes=32 time Reply from 172.16.6.20: number of bytes=32 time Reply from 172.16.6.20: number of bytes=32 time The utility displays the IP address and name of the host being checked (the IP address is always displayed, the name is only displayed when the -a parameter is specified). For each packet sent, information about the size, response time, and lifetime is displayed. After this, statistics are displayed: the number of sent, received and lost packets, the percentage of losses, the minimum, maximum and average response time. If you use large enough packets and send a large number of requests, you can roughly estimate the quality of the communication channel. If it is impossible to check the availability of the host, the utility displays error information. Below is an example of the response of the ping utility when trying to send a request to a non-existent host. Exchange of packets from 172.16.6.21 to 32 bytes:
Ping statistics for 172.16.6.21: Approximate transmission and reception times: The utility does not report the absence of a host, but rather that a response to the sent request was not received within the allotted time. The reason for this is not necessarily the absence of a host on the network. The problem may lie in communication failures, overload or incorrect setting routers, etc. tracert utility. Utility tracert designed to explore the route to remote host. It has the following syntax: tracert [-d] [-h number of nodes] [-j list of nodes] [-w timeout] hostname Description of utility keys tracert shown in the table: Utility tracert displays information about all routers through which packets destined for a specified host pass. The tracert utility uses the same protocol (ICMP) as ping, sending 3 requests to each router. Route information is displayed in a form similar to the ping utility. Below is a typical example response from the tracert utility. Route tracing to zecke.demos.su 1 2 3 20 ms 30 ms 20 ms moscow2-fa1-0-0.sibintek. net Tracing is complete. The utility displays the name and IP address of the host being examined. For each router, the step number, response speed to all three requests sent, the name and IP address of the router are displayed. If one of the ping requests remains unanswered, an asterisk is displayed in the corresponding column instead of the response time. If the -d option is specified or the utility is unable to obtain the hostname, only the IP address of the corresponding router is displayed in the table. This utility allows you to determine the problem area on the path to the host under study (both the location of the break and the location of deteriorating connection quality). The first is determined by the lack of response after a certain router, the second by a significantly increased response time. If one of the route nodes fails, the tracert utility, like ping, reports no response from the host: Trace route to cnn.com 1 10 ms 2 3 4 170 ms 160 ms 140 ms sibinternet-lgw.Moscow.ST. NET Tracing is complete. No response from host in global network does not yet mean that it is unavailable. Many large companies now block ICMP replies from being sent to received requests, which leads to the result shown above. For this reason, when testing routes and WAN access, you should use host addresses that do not block ICMP requests. arp utility Utility arp is designed to view the table of correspondence between IP addresses and MAC addresses and make changes to this table. It has the following syntax: arp -s ip_address mac_address [interface_address] Description of utility keys arp shown in the table:
Below is an example of an ARP table output by using the arp -a command. Interface: 172.16.6.196 on Interface 0x1000003 Hostname utility. Utility hostname is intended to display the name local computer. It has no parameters and displays only the name of the local computer. Using this utility, you can quickly find out the computer name without resorting to Control panels. route utility Utility route designed to work with a local routing table. It has the following syntax:
The PRINT and DELETE commands allow the use of wildcards when specifying the destination host or gateway. The gateway parameter can be omitted for these commands. When adding or changing routes, the route utility checks the entered information for compliance with the condition (NODE & MASK) == NODE. If this condition is not met, the utility displays an error message and does not add or change the route. The utility searches for network names in the networks. Gateway names are searched in hosts file. Both files are located in the %systemroot%\system32\drivers\etc folder. The presence and completion of these files is not necessary for the normal functioning of the route utility and routing. Below is a routing table specific to a Windows XP Professional workstation:
The table does not contain permanent routes and is generated by the OS at the time of initialization of the TCP/IP stack. Although in most cases this is not required on a workstation, you can manually edit routing tables. Below is an example of adding a new route and the routing table after adding: route add 172.16.6.0 MASK 255.255.255.0 172.16.11.1 METRIC 1 IF 0x1000003 =========================================================== The added route is highlighted in red. IN in this example added route to network 172.16.6.0/24 via gateway 172.16.11.1. The computer's network adapter is specified as the interface. Adding this route was not necessary, since access to all networks other than 172.16.11.0/24 is still carried out through the 172.16.11.1 gateway. nslookup utility. Utility nslookup is designed to perform requests for name resolution to IP addresses to DNS servers. The utility is quite complex and contains its own command interpreter. Below we will consider only the simplest way to call nslookup, sufficient to check the operation of DNS. In the simplest case, the utility nslookup has the following syntax: nslookup [host [server]] Description of utility keys nslookup shown in the table. For example, when you enter the command nslookup center.fio.ru The utility displays the following information about the host: Server: net-server.net.fio.ru Name: msk-server-ext2.msk.net.fio.ru The first two lines of the response contain the name and IP address of the DNS server that was used to resolve the name. The next line contains the real DNS name of the host and its IP address. There may also be an Aliases line that contains alternative names the same host. Any host has an A record on one or more DNS servers. For the convenience of users and to simplify the administration of a DNS zone, CNAME records are often used, which are links to A records. This allows one host to be given multiple symbolic names, but when the host's IP address changes, only one entry (A) needs to be changed. The nslookup utility specifies its A record as the host's primary name, and all names assigned to the host through CNAME records are indicated in the line Aliases. If as the first parameter to the utility nslookup specify not the host name, but the domain name, then the utility will simply check the existence of such a domain: Server: net-server.net.fio.ru If it is impossible to convert the name to an IP address, the utility nslookup reports that the specified domain was not found: Server: net-server.net.fio.ru *** net-server.net.fio.ru can"t find test.center.fio.ru: Non-existent domain The message that a name cannot be resolved to an IP address is usually a result of an incorrect host name or a missing host name. To get acquainted with the command mode of the utility nslookup, enter the command at the command line nslookup without parameters. When prompted to enter commands, nslookup, enter help and press Enter. A hack employee is a disaster for any enterprise or company. Therefore, the question constantly arises of how to monitor an employee’s work computer and ensure that there are no unauthorized actions. Let us immediately note that the employee must be informed (in writing, with a signature) that covert surveillance of the computer on the local network is being conducted. Perhaps only this fact will help to avoid violations and put the employee on the path of a “hard worker.” If not, then here is a solution for complete control over computers on your local network. So, software called “Mipko Employe Monitor” - a version specifically for corporate networks. After installation and launch, and you can run it from the desktop or by pressing “ctrl+alt+shift+k”, you need to configure the user interface - what exactly needs to be monitored and controlled on the local network.
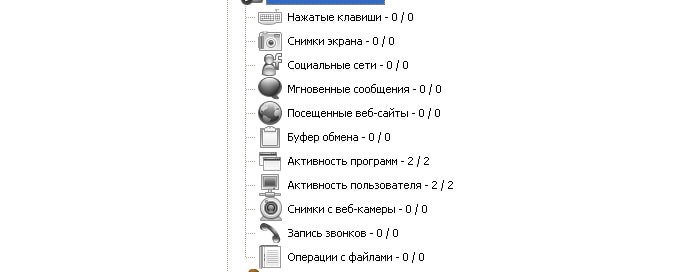
Monitoring allows you to track the following actions:
Quite extensive functionality. The main thing that an employer is usually interested in when monitoring users on a local network is screenshots and websites visited. In order not to face claims of interference with personal information (for example, if you set up a view of the web pages you visited and saw personal correspondence on social networks), set the blocking of all social networks and chats, as well as a ban on installing third-party software - only what is required for work. Remote monitoring of a computer on a local networkAs a rule, the employer is interested in only two aspects - a screenshot of the local network user’s computer and his viewing of web pages (as mentioned above, employees are familiar with this information).
That's it, now the employees are, as they say, “Under the hood” - you can monitor the users of the local network. ipconfig, ping And tracert.1. PURPOSE OF THE WORK Defining settings for connecting to a local network and the Internet using the utility ipconfig. Study of probabilistic-time characteristics of Internet fragments using the utility ping. Studying the topology of Internet network fragments using the utility tracert . 2. METHODOLOGICAL INSTRUCTIONS FOR PERFORMING LABORATORY WORK 2.1. Addressing in IP networks 2.1.1. Address types: physical (MAC address), network (IP address) and symbolic (DNS name) Each computer on a TCP/IP network has three levels of addresses: · The local address of the node, determined by the technology with which the separate network to which this node belongs is built. For hosts included in local networks, this is the MAC address of the network adapter or router port, for example, 11-A0-17-3D-BC-01. These addresses are assigned by equipment manufacturers and are unique addresses because they are managed centrally. For all existing local network technologies, the MAC address has a 6-byte format: the upper 3 bytes are the manufacturer’s company identifier, and the lower 3 bytes are assigned uniquely by the manufacturer itself. · IP address consisting of 4 bytes, for example, 109.26.17.100. This address is used at the network layer. It is assigned by the administrator during the configuration of computers and routers. An IP address consists of two parts: the network number and the host number. The network number can be chosen arbitrarily by the administrator, or assigned on the recommendation of a special Internet division (Network Information Center, NIC), if the network must operate as an integral part of the Internet. Typically, Internet Service Providers obtain address ranges from NICs and then distribute them to their subscribers. The host number in the IP protocol is assigned independently of the local address of the host. The division of the IP address into the network number and host number fields is flexible, and the boundary between these fields can be set quite arbitrarily. A node can be part of several IP networks. In this case, the node must have several IP addresses, according to the number of network connections. Thus, the IP address does not characterize a single computer or router, but one network connection. · Symbolic identifier-name, for example, SERV1.IBM.COM. This address is assigned by the administrator and consists of several parts, for example, machine name, organization name, domain name. This address, also called a DNS name, is used at the application level, for example, in the FTP or telnet protocols. 2.1.2. Three Main Classes of IP Addresses An IP address is 4 bytes long and is usually written as four numbers representing the value of each byte in decimal form, separated by periods, for example: 128.10.2.30 - traditional decimal form of address representation, 10000000 00001010 00000010 00011110 - binary form of representation of the same address.
The address consists of two logical parts- network numbers and node numbers in the network. Which part of the address relates to the network number, and which part to the node number, is determined by the values of the first bits of the address: · If the address starts with 0, then the network is classified as class A, and the network number occupies one byte, the remaining 3 bytes are interpreted as the node number in the network. Class A networks have numbers ranging from 1 to 126. (Number 0 is not used, and number 127 is reserved for special purposes, as discussed below.) In Class A networks, the number of nodes should be greater than 2 16, but not exceed 2 24 . · If the first two bits of the address are equal to 10, then the network belongs to class B and is a medium-sized network with the number of nodes 2 8 - 2 16. In class B networks, 16 bits, that is, 2 bytes, are allocated for the network address and for the node address. · If the address begins with the sequence 110, then this is a class C network with no more than 2 8 nodes. 24 bits are allocated for the network address, and 8 bits for the host address. · If the address begins with the sequence 1110, then it is a class D address and denotes a special, multicast address. If a packet contains a class D address as a destination address, then all nodes to which this address is assigned must receive such a packet. · If the address begins with the sequence 11110, then it is a class E address and is reserved for future use. The table shows the ranges of network numbers corresponding to each class of networks. 2.1.3. Mapping symbolic addresses to IP addresses: DNS service DNS (Domain Name System) is a distributed database that supports a hierarchical naming system for identifying nodes on the Internet. DNS service intended for automatic search IP addresses by known symbolic host name. The DNS specification is defined by RFC 1034 and 1035. DNS requires a static configuration of its tables that map computer names to IP addresses. The DNS protocol is an application layer service protocol. This protocol is asymmetrical - it defines DNS servers and DNS clients. DNS servers store part of distributed base data on the correspondence of symbolic names and IP addresses. This database is distributed across administrative domains of the Internet. Clients DNS server know the IP address of the DNS server of their administrative domain and send a request via the IP protocol in which they report a well-known symbolic name and ask to return the corresponding IP address. If the data about the requested match is stored in the database of this DNS server, then it immediately sends a response to the client, but if not, then it sends the request to a DNS server of another domain, which can process the request itself or transfer it to another DNS server. All DNS servers are connected hierarchically, in accordance with the Internet domain hierarchy. The client queries these name servers until it finds the mappings it needs. This process is accelerated by the fact that name servers continually cache the information provided by queries. Client computers can use the IP addresses of several DNS servers in their work to increase the reliability of their work. The DNS database has a tree structure called a domain namespace, in which each domain (node in the tree) has a name and can contain subdomains. The name of a domain identifies its position in this database in relation to the parent domain, with dots in the name separating the parts corresponding to the nodes of the domain. The DNS database root is managed by the Internet Network Information Center. Domains top level are assigned on a country-by-country basis as well as on an organizational basis. The names of these domains must follow the international standard ISO 3166. Three-letter and two-letter abbreviations are used to designate countries, and various types organizations use the following abbreviations: · com - commercial organizations (for example, microsoft.com); · edu - educational (for example, mit.edu); · gov - government organizations (for example, nsf.gov); · org - non-profit organizations (for example, fidonet.org); · net - organizations that support networks (for example, nsf.net). Each DNS domain is administered by a separate organization, which typically splits its domain into subdomains and delegates the administration of those subdomains to other organizations. Each domain has unique name, and each of the subdomains has a unique name within its domain. The domain name can contain up to 63 characters. Each host on the Internet is uniquely identified by its complete domain name(fully qualified domain name, FQDN), which includes the names of all domains in the direction from host to root. Example of a fully qualified DNS name: server.aics.acs.cctpu.edu.ru 2.1.4. Automation of the process of assigning IP addresses to network nodes - DHCP protocol IP addresses can be assigned manually by the network administrator. This is a tedious procedure for the administrator. To complicate matters further, many users do not have sufficient knowledge to configure their computers to work on the Internet and must therefore rely on administrators. Protocol Dynamic Host Configuration Protocol (DHCP) was designed to free the administrator from these problems. The main purpose of DHCP is to dynamically assign IP addresses. However, in addition to dynamic, DHCP can support more simple ways manual and automatic static assignment of addresses. In the manual procedure for assigning addresses, the administrator takes an active part, providing the DHCP server with information about the correspondence of IP addresses to physical addresses or other client identifiers. These addresses are provided to clients in response to their requests to the DHCP server. In the automatic static method, the DHCP server assigns an IP address (and possibly other client configuration parameters) from a pool (set) of available IP addresses without operator intervention. The boundaries of the pool of assigned addresses are set by the administrator when configuring the DHCP server. There is still a constant mapping between the client ID and its IP address, as with manual assignment. It is set when the DHCP server first assigns an IP address to the client. For all subsequent requests, the server returns the same IP address. With dynamic address allocation, the DHCP server issues an address to the client for a limited time, which makes it possible to subsequently reuse IP addresses by other computers. Dynamic address division allows you to build an IP network, the number of nodes in which far exceeds the number of IP addresses available to the administrator. 2.2. System utilities network diagnostics 2.2.1. Utility ipconfig The ipconfig (IP configuration) utility is designed to configure the IP protocol for operating system Windows. In this laboratory work This utility will only be used to obtain information about the local network connection. To get this information, go to Start → Run → cmd and at the command prompt enter: In the "Adapter" section Ethernet Connection over local network" for this lab the fields "DHCP", "IP address" and "DNS servers" will be required. 2.2.2. ping utility The ping (Packet Internet Groper) utility is one of the main tools used for debugging networks and is used to force a response from a specific machine. It allows you to check the operation of TCP/IP programs on remote machines, device addresses on the local network, address and route for remote network device. The ping command involves the routing system, address resolution schemes, and network gateways. This is a low-level utility that does not require the presence of server processes on the machine being tested, so a successful result when passing a request does not mean that any service programs high level, but indicates that the network is in working condition, the power of the machine being tested is turned on, and the machine has not failed (“does not hang”). IN Windows utility ping is included in the package and is a program that can be launched from the command line. Requests from the ping utility are sent using the Internet Control Message Protocol (ICMP). Having received such a request, the software that implements the IP protocol at the recipient sends an echo response. If the machine being scanned was loaded with higher-priority work at the time the request was received (for example, processing and redirecting a large volume of traffic), then the response will not be sent immediately, but as soon as the higher-priority task is completed. Therefore, it should be noted that the delay calculated by the ping utility is caused not only throughput the data transmission channel to the machine being tested, but also the workload of this machine. Echo requests are sent a specified number of times (switch -n). By default, four requests are sent, after which statistics are displayed. Note: because from the utility ping begins hacker attack, some servers may not send echo replies for security reasons (for example, www . microsoft . com ). Don't wait in vain, enter the interrupt command ( CTRL + C ). Command Format: ping [-t][-a][-n][-l][-f][-i TTL][-v TOS] [-r][machine name][[-j Node list]|[-k Node list]][-w] Ping utility parameters In practice, most of the options in the command format can be omitted, then the command line can be: ping hostname (to loop the output of connection information, use the option - t; to display information n times, use the –n number of times option). Example : ping –n 20 peak.mountin.net Exchange of packets with peak.mountin.net of 32 bytes: Response from 207.227.119.2: number of bytes=32 time=734ms TTL=231 Timed out request. Response from 207.227.119.2: number of bytes=32 time=719ms TTL=231 Response from 207.227.119.2: number of bytes=32 time=1015ms TTL=231 Timed out request. Response from 207.227.119.2: number of bytes=32 time=703ms TTL=231 Response from 207.227.119.2: number of bytes=32 time=688ms TTL=231 Response from 207.227.119.2: number of bytes=32 time=782ms TTL=231 Response from 207.227.119.2: number of bytes=32 time=688ms TTL=231 Response from 207.227.119.2: number of bytes=32 time=688ms TTL=231 Response from 207.227.119.2: number of bytes=32 time=688ms TTL=231 Timed out request. Response from 207.227.119.2: number of bytes=32 time=687ms TTL=231 Response from 207.227.119.2: number of bytes=32 time=735ms TTL=231 Response from 207.227.119.2: number of bytes=32 time=672ms TTL=231 Response from 207.227.119.2: number of bytes=32 time=704ms TTL=231 Ping statistics for 207.227.119.2: Packets: sent = 20, received = 16, lost = 4 (20% loss), Approximate transmission and reception times: lowest = 672ms, highest = 1015ms, average = 580ms An example of determining a host name from an IP address ping –a 194.67.57.26 Exchange of packets with mail.ru of 32 bytes: ... 2.2.3. tracert utility The tracert utility allows you to identify the sequence of routers through which an IP packet passes on the way to its destination. Command Format: tracert machinename machine_name can be the hostname or IP address of the machine. The output is a list of machines, starting from the first gateway and ending with the destination. Example: tracert peak.mountin.net Route trace to peak.mountin.net with a maximum number of jumps of 30:
Tracing is complete. Packets are sent in threes to each node. For each packet, the screen displays the time interval between sending the packet and receiving the response. The * means that no response was received for this packet. If the node does not respond, then if the response timeout is exceeded, the message “Request timeout exceeded” is displayed. The response interval can be changed using the –w option of the tracert command. The tracert command works by setting the time-to-live (hop count) field of an outgoing packet so that the time expires before the packet reaches its destination. When the lifetime expires, the current gateway will send an error message to the source machine. Each increment of the time-to-live field allows the packet to travel one router further. Note: To output information to a file, use the output redirection symbol ">". This symbol is also valid for the ping and tracert . Example: tracert 195.208.164.1 > tracert.txt A route trace report to the specified node will be placed in the tracert.txt file. 3. LABORATORY WORK TASK The laboratory work report must be prepared in OpenOffice Word or MS Word. The report file must be named in the following format: "LABORATORY GROUP NUMBER FULL NAME1 FULL NAME2", for example: "1 8820 Ivanov A.S. Petrov V.M." The report file must be copied to the folder "\server\Student\Student\For exchange\Internet technologies". You can place an image of the current window in the report in the following way: press ALT+PrintScreen, go to the editor and press CTRL+V. You can copy text from the command line window as follows: select the required text with the mouse and right-click on the selected area, then go to text editor and press Ctrl+V. The list of node addresses for all options is given in the 4th paragraph. 3.1. Using the ipconfig utility, determine the IP address and physical address of the main network interface of the computer, the IP address of the gateway, the IP addresses of DNS servers and whether DHCP is used.. Present the results in table form . 3.2. Check the connection status with any two nodes (working) in accordance with the task option. The number of requests sent must be at least 20. As a result, reflect for each of the nodes being studied in the form of a table : a. percentage of lost packets; b. average reception and transmission time; c. the number of routers (including the gateway) to the polled node; d. Host IP address. e. class of the network to which this node belongs; f. hostname derived from the host's IP address. The report should explain how the values were determined. 3.3. Trace two operational nodes in accordance with the task option. Record the results in a table. If the transit times of three packets differ by more than 10 ms, or if there are packet losses, then for the corresponding nodes the average transit time must be determined using the ping utility using 20 packets. . Based on the results of the table in the report, provide schedule changes in the average packet transit time. In the report, provide one copy of the window with the results of the tracert command. For each node being polled, determine the section of the network between two neighboring routers, which is characterized by the greatest delay when sending packets. For found routers using Whois service determine the name of the organization and contact information (tel., email). The information received must be included in the report. |
| Read: |
|---|
New
- How to use Google Photos, overview of Google foto login functions
- Payment system Payza (ex-Alertpay) Payza login to your personal account
- How to open APK and how to edit?
- Review of the Alpha GT smartphone from Highscreen Packaging and delivery
- Official LG firmware via KDZ
- What is an SSD and how to install it?
- How to put an accent on a letter in Word
- How to convert images to PNG format?
- Technical problems and their solutions v
- Bioshock remastered won't start