Sections of the site
Editor's Choice:
- BIOS beeps when turning on PC
- How to delete a page in a contact?
- How to delete a deleted VKontakte page?
- ENIAC - the very first computer in the world
- VKontakte was blocked at work, how can I get around it?
- How to delete a VKontakte page from your phone
- Methods to format a hard drive using BIOS
- How to log into Odnoklassniki if the site is blocked?
- How to permanently delete a page in contact?
- How to bypass VK and Odnoklassniki blocking in Ukraine
Advertising
| How to recover files after encrypting the WannaCry ransomware virus |
|
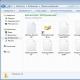
Sandbox funny barbel May 18, 2017 at 09:52How to recover files after encrypting the WannaCry ransomware virusGood afternoon, Habrazhiteliki. A lot has been written on Habré about how to protect yourself from WannaCry. But for some reason, nowhere was it explained how to return encrypted data. I want to fill this gap. And shed a little light on how we did this in our “well-known” company involved in logistics. This is more of an instruction for our information security administrators. Recovery after data encryptionThis is not Decryption, but rather Recovery. And it only works if shadow copying is enabled in windows, i.e. Data can be restored from Windows restore points itself. Select a recovery point and you can export files and directories to the location you need:
Select those files that are not yet encrypted and export them to the location you need. (In some cases, when the update has already passed, those recovery points may be overwritten when the files were not yet encrypted. It is also possible that some of the data is already encrypted in the recovery points, but some is not yet. You need to restore only what can be restored.)
That, in principle, is all that is required for restoration where possible. Important! After restoring files, you need to erase those recovery points where the data was already encrypted. It has been noticed that this is where the virus restores itself after cleaning. Recover data, as well as neutralize and remove the virus:1. Disconnect your computer from the network2. Next, you need to use the utility wann_kill_v_(version number) - this utility kills the virus process. The virus signatures themselves remain stored in the system. We do this because when you bring a flash drive to the computer that needs to be disinfected, the virus encrypts the flash drive. It is important to run this utility before the virus gets onto the flash drive.
3. Clean your Computer using DrWeb CureIt (here the virus itself is removed from the computer) 4. Recover the data you need as described above “ After data encryption» 5. (Only after data recovery) Destroy recovery points, because this is where the virus restores itself after cleaning.
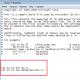
System protection:
Tune:
Delete. 6. Then roll out the KB4012212 patch, thereby closing the MS17-010 network vulnerability That's basically how I fought the Wanna Cry virus. Tags: WannaCry, Decryption |
| Read: |
|---|
Popular:
Temporary email for 10 minutes?
|
New
- How to delete a page in a contact?
- How to delete a deleted VKontakte page?
- ENIAC - the very first computer in the world
- VKontakte was blocked at work, how can I get around it?
- How to delete a VKontakte page from your phone
- Methods to format a hard drive using BIOS
- How to log into Odnoklassniki if the site is blocked?
- How to permanently delete a page in contact?
- How to bypass VK and Odnoklassniki blocking in Ukraine
- Formatting via BIOS